Brave Readers Continue…
During a internal pentest, I found an issue where the “Everyone” group in Active Directory had “FullControl” over the root of the domain. After I picked my jaw up off the floor, I quickly validated it with another tool. That tool, and the discoveries I made afterwards with that tool, are the reason for this article.
My mission is to identify vulnerabilities and misconfigurations that traditional tools and traditional means cannot find.
That’s what this article is all about. I want to share a neat Active Directory security tool and how you can use it to find hidden vulnerabilities. It’s a tool I wish I had 10 years ago. I truly believe all IT admins, Sysadmins, Pentesters and anyone else who manages Active Directory will get value from this post. Let’s get into it!
What is ADeleg?
Straight from GitHub, created by Matthieu Buffet, ADeleg is an Active Directory delegation management tool. It allows you to make a detailed inventory of delegations set up so far in a forest, along with their potential issues, such as:
- Objects owned by users
- Objects with ACEs for users
- Non canonical ACL
- Disabled ACL inheritance
- Default ACL modified in schema
- Deleted delegation trustees
Pretty cool right? What’s also cool is that the GUI looks and feels like Active Directory Users and Computers [ADUC for those so inclined ;0)], so sysadmins should be right at home.
So to really understand the true power of this tool from a security perspective we have to understand what a delegation is. So let’s cover that briefly.
What is Delegation?
Delegation’s allow for assigning specific permissions to specific users to be able to perform specific tasks without requiring them to be a member of privileged security groups such as Domain Admins. This is best explained with an example.
Let’s say you have a group of IT users who perform Help Desk related duties. You want them to be able to reset users passwords in the event that a user is locked out of their account. by default in Active Directory only members of the “Domain Admins” group and the “Account Operators” group have the ability to reset passwords for user accounts. (The user has the ability to reset their own password too of course, but we’re talking about Help Desk for now)
In order to maintain least privilege and a secure tiered administration model, you don’t want Help Desk technicians to also be members of Domain Admins. That would be way too much permission and break your tiered admin model. So what do you do? That’s right, delegate some permissions!
Those permissions end up being delegations that we can then audit, inspect and analyze. That’s where ADeleg comes in. By the way if you want additional information on delegating administration, check out Microsoft’s documentation.
Now that we’ve covered what a delegation is (at a high-level) let’s talk about some common misconfigurations, what to look for and how to find them.
Common Delegation Misconfigurations
There are two categories of objects within ADeleg, Resources and Trustees. As a result there are two categories of misconfigurations I look for when using ADeleg.
- Privileged resources that have unnecessary or insecure delegations. Example: The root domain (acme.local) resource that allows “Everyone” “FullControl”
- Low privilege trustees that have unnecessary or insecure delegations. Example: “Domain Users” that have “WriteAllProperties” on the “Domain Admins” group
Now if you have already downloaded and opened the tool, you may be wondering, there is a lot of stuff in there especially for big environments. How on earth do I go through it all and how do I identify issues I should be concerned with?
The first thing I would recommend is focusing on the highest privileged resources and the lowest privileged trustees. Let me explain what I mean.
- Highest privileged resources: Think tier 0 groups, users and containers. Domain Admins, Enterprise Admins, Domain Controllers, jump boxes, IT admin workstations, critical servers, etc.
- Lowest privileged trustees: This would be non-administrative groups, users and containers. Domain Users, Everyone, Authenticated Users, end-user computers, etc.
Which category you start with doesn’t matter, so continue reading to learn how to use ADeleg to identify misconfigured delegations.
How To Find Delegation Misconfigurations With ADeleg
Step #1 is opening ADeleg and clicking Connect to connect ADeleg to Active Directory. If you’re on a non-domain joined host you will need to click “use a specific domain controller”, enter the authentication information, then click Connect.
Checking Trustees for misconfigured permissions
I like to start with Trustees, so the first thing I do is click:
View → Index view by… → Trustees.
That puts the trustees on the left hand side and the resources on the right. That way I can click on a trustee and see the permissions it has on a given resource.
Then on the left hand side, I open up the Global dropdown and look for several key trustees:
- Everyone
- Authenticated Users
- Domain Users
- Pre-Windows 2000 Compatible Access
- Any other low-privilege trustee…
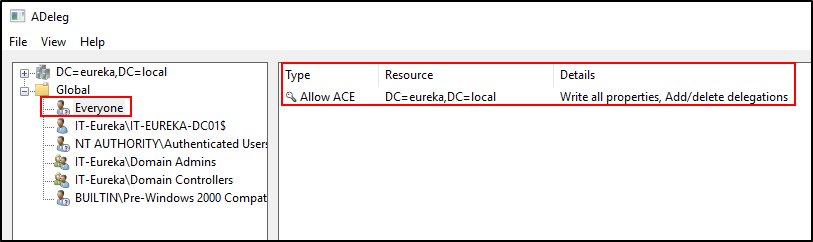
As you can see in the two screenshots below, we have a bit of an oopsie. The first screenshot is showing what I talked about earlier in this article. The “Everyone” group has permissions to ‘write all properties’ and to ‘add/delete delegations’.
The next screenshot also shows a potential issue. “Domain Users” may have the ability to reset passwords on all child user objects in the Admins OU. That sounds kind of bad…
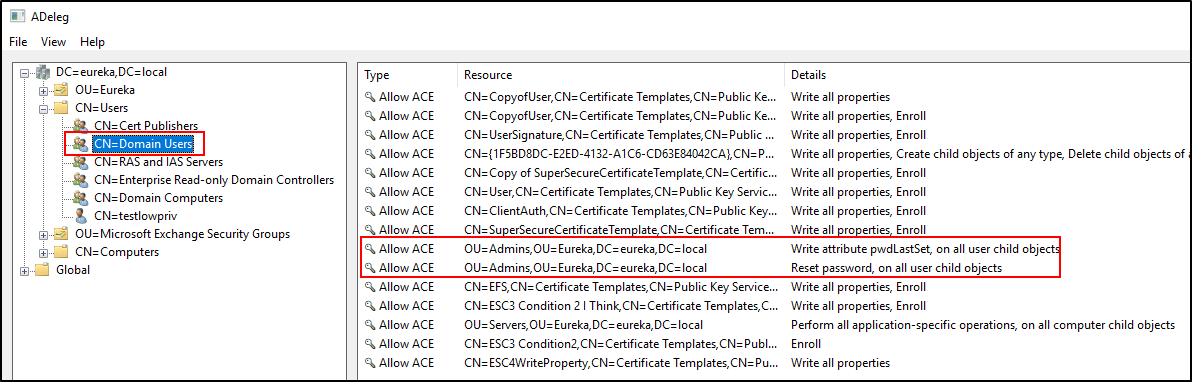
What’s also neat is that you can detect potentially misconfigured certificate templates using ADeleg as well. Note that it’s not perfect and there are false positives.
I go through the same process for each of the trustees listed above. I review the permissions granted on the resources in the window on the right and look for permissions that may be dangerous. I’m looking for things like:
- Write all properties
- Create/delete child objects
- Ownership of a resource
- Add/delete delegations
- Write attribute
- Validated write
- Change the owner
- Change password
- Reset password
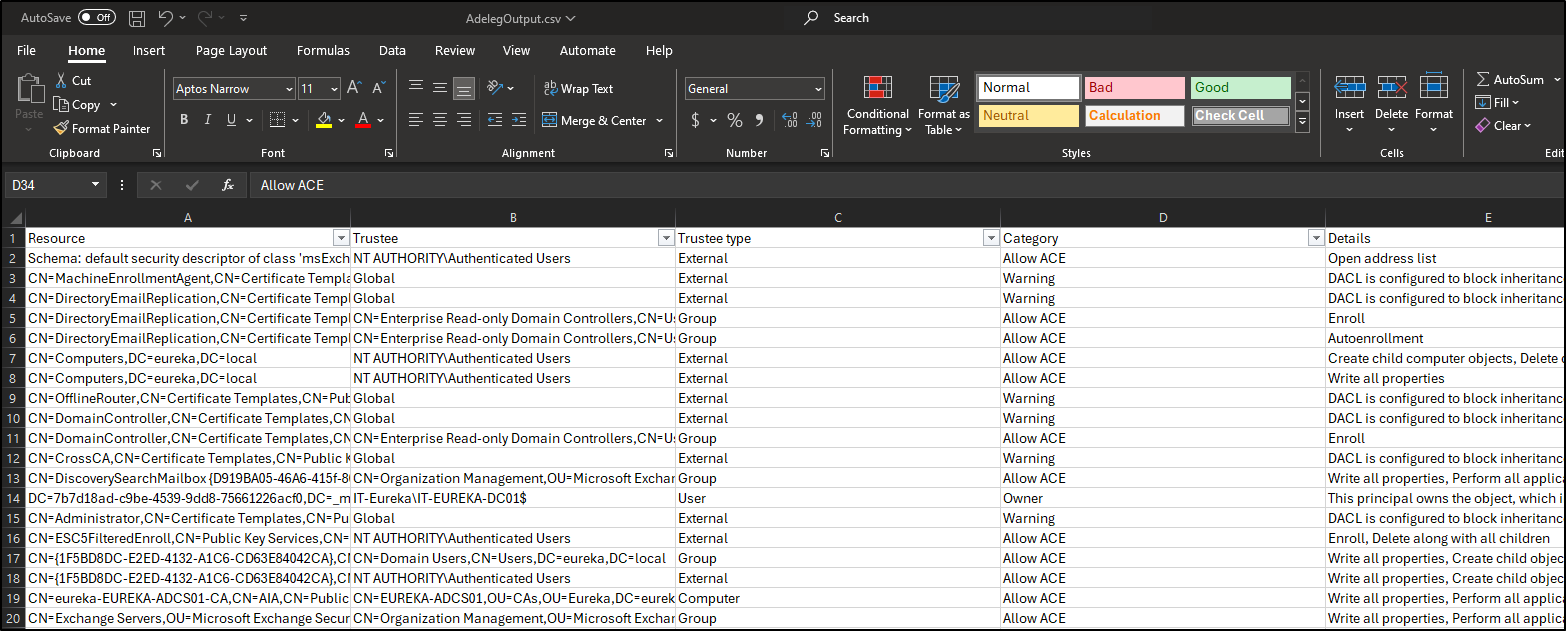
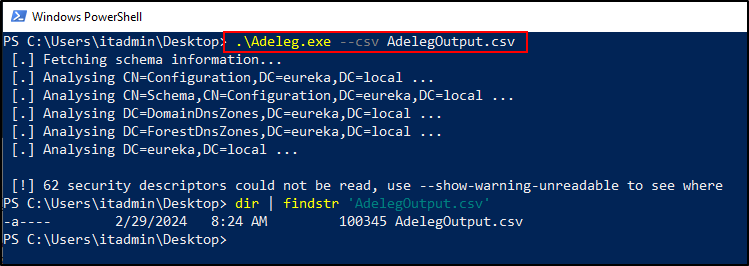
As you can see, sometimes the entire list of permissions is not able to be displayed. In this case, it’s helpful to use ADeleg from the command line and export the full delegation list as a csv. To view the ADeleg help menu, type ADeleg.exe -h.

To export all delegations to a file type Adeleg.exe –csv ADelegOutput.csv. Then you can open the csv file up in excel and filter and analyze the delegations to your heart’s content. Sorting and reviewing these delegations is A LOT easier in excel. 😎
Checking Resources for misconfigured permissions
The next thing I do is to check for misconfigured delegations on resources. To revert the view back to index by resource, click View → Index view by.. → Resources. Then I review tier 0 resources, like I mentioned above. Now if you want a deep dive on Tier 0, check out this article by Jonas Bülow Knudsen from SpectreOps. I’m looking at things like:
- Domain root object
- Built-in Administrator groups like Administrators, Domain Admins, Enterprise Admins, Account Operators, Backup Operators etc.
- Domain Controllers group
- Domain Controllers OU
- krbtgt
- Users container
- and much more…
Here’s an example of the “Everyone” issue just in reverse. You can also see there may be some other trustees that may have insecure delegations…
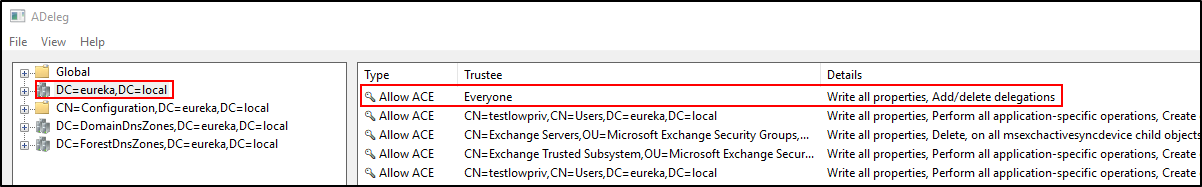
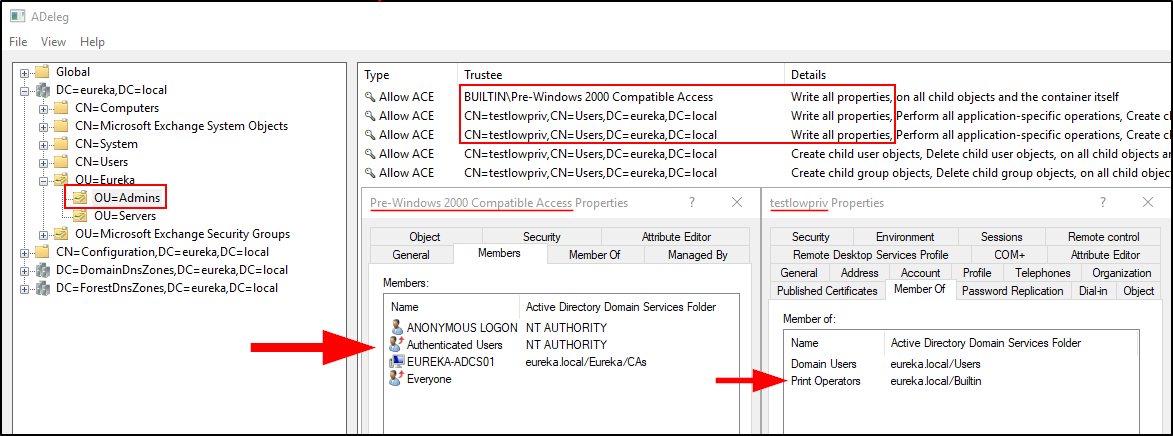
Here’s another example. Can you spot the issue?
As you can see, the “Pre-Windows 2000 Compatible Access group” as well as the user “testlowpriv” have delegations on an Admin OU that are both not default and definitely insecure. Upon review of the group membership for each there were further issues identified. These are issues we may not have been aware of or able to identify if we were not specifically looking for them.

For The Overachievers – A tool to help find insecure delegations
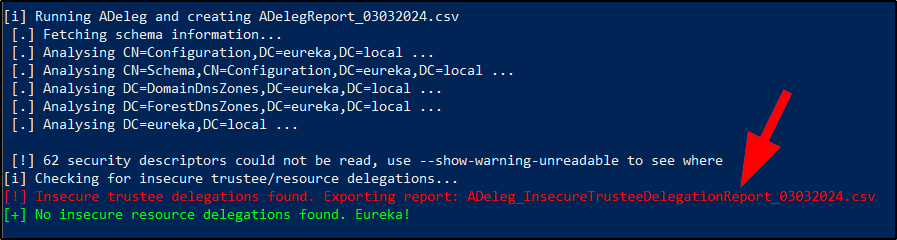
- Runs ADeleg and generates a csv report
- Reads the report and tries to identify insecure trustee and resource delegations
- If any issues are found, it generates a csv report with only the insecure configurations
Once you download Invoke-ADeleginator.ps1, dot source it using . .\Invoke-ADeleginator.ps1. Then run it with Invoke-ADeleginator.
ADeleginator is currently able to find many of the common insecure configurations that I typically see. I plan to add more over time, however, if you notice there’s something missing or have any feedback or requests, please do let me know!
Those With Courage…
So there you have it! That’s my rundown on the wonderful ADeleg tool and how you can use it to identify misconfigured delegations in Active Directory.
If you made it this far, thank you for reading! I hope you got value from this article. What I have demonstrated here only scratches the surface. This is a tool I use on every single internal pentest engagement. It’s helped me identify very serious delegation issues and it’s helped numerous clients identify issues quicker and more accurately.
If you’re an IT Admin, Sysadmin, Security Analyst, Pentest, or if you manage or secure or assess Active Directory in any way, ADeleg can be a really valuable tool to add to your toolbelt. I hope you consider trying it out!
Lastly, please do check out the resources, there is a wealth of information there that simply cannot be covered in one blog post alone. 🙏
Resources
- ADeleg – The fantastic Active Directory delegation tool by Matthieu Buffet
- Microsoft Delegated Admin Documentation
- Tier 0 Blog Posts An excellent journey of learning about Tier 0 by Jonas Bülow Knudsen
- ADeleginator by yours truly Spencer Alessi
- If you’re looking for expert insights into all things Active Directory security, the amazing adsecurity.org blog by Sean Metcalf is an absolute 💎
- This whitepaper is an excellent deep dive into object ownership issues in Active Director. Trimarc Whitepaper: Owned or Pwned by Jim Sykora