In this episode Brad and Spencer discuss the THREE primary ways we gain initial access on penetration tests and how to stop […]
Subscribe to the CyberThreatPOV Podcast
9-16-22 Week in Review: Uber Hacked, Teams Cleartext Tokens, Intermittent Ransomware Encryption
In this week’s review Uber was hacked Microsoft Teams stores auth tokens as cleartext in Windows, Linux, Macs Ransomware Developers Turn to Intermittent Encryption […]
Episode 7: How to Make Threat Actors Cry
In this episode Brad and Spencer talk about what mature, proactive organizations are doing to harden and secure their environments, with the end goal […]
9-9-22 Week In Review: New EvilProxy Phishing Service and Linux Malware
In this week’s review: New EvilProxy Phishing Service Allowing Cybercriminals to Bypass 2-Factor Security New Linux Malware Evades Detection Using Multi-stage Deployment If you’re […]
Episode 6: 5 Ways to Get More Value out of your External Penetration Test
Are you sure you’re getting what you paid for when it comes to external penetration tests? In this podcast Brad and Spencer discuss 5 […]
9-2-22 Week in Review: Okta Phishing, BEC Analysis, LNK Attacks
In this week’s review Roasting 0ktapus: The phishing campaign going after Okta identity credentials Advanced BEC Scam Campaign Targeting Executives on O365 The Rise […]
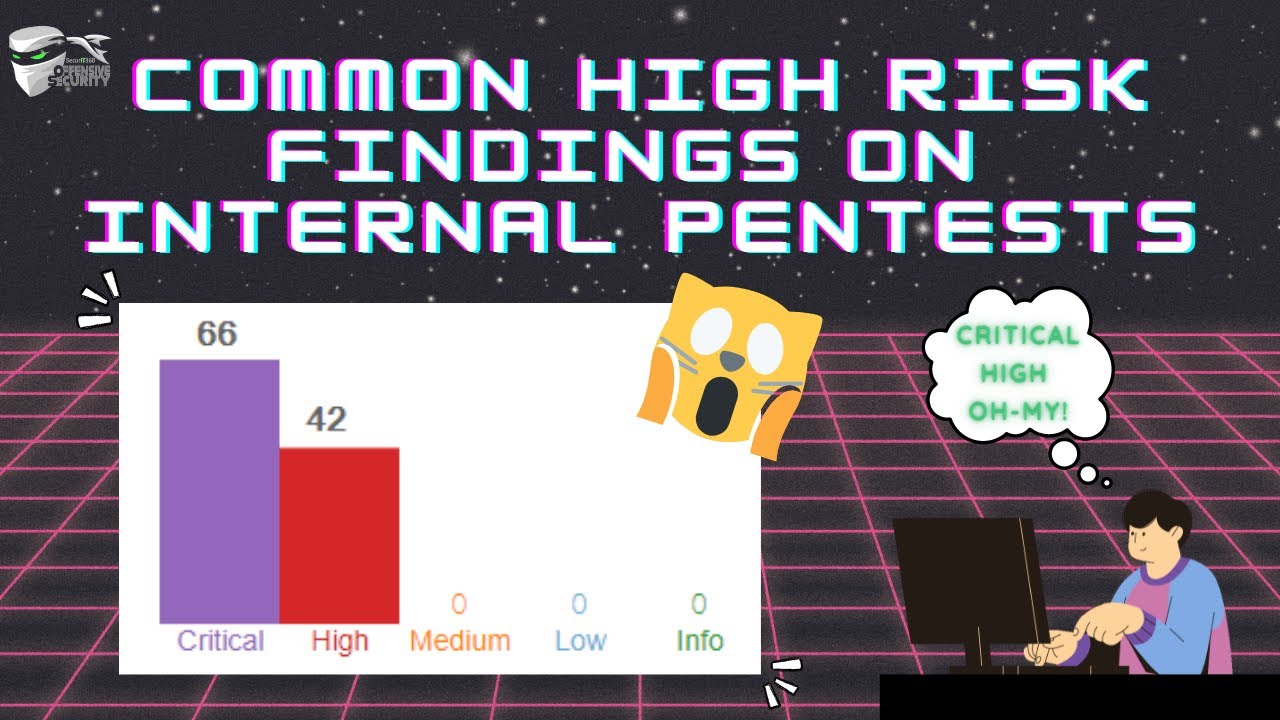
Episode 5: Common High-Risk Findings on Internal Pentests
It’s an unfortunate truth that we see these common high risk findings time and time again on internal pentests. We find these issues on […]
8-26-22 Week in Review: LastPass Breach, Office 365 Abuse, DevSecOps
In this week’s review Hackers Breach LastPass Developer System to Steal Source Code You Can’t Audit Me: APT29 Continues Targeting Microsoft 365 | Mandiant […]
Episode 4: 7 Awesome Ways to Show Off Your Skills as a Pentester
In order to stay relevant and up-to-date with new techniques and tools, it requires a certain amount of focus day after day, week after […]
8-19-22 Week in Review: Password Snooping, Supply Chain, Cl0p Ransomware
In this week’s review Cleartext Shenanigans: Gifting User Passwords to Adversaries With NPPSPY Realtek SDK Vulnerability Exposes Routers InfoSec Handlers Diary Blog – SANS […]