Organizations and individuals must strengthen their security measures and Multi-factor authentication (MFA) is one of the most effective ways to protect accounts from unauthorized access. While traditional push notification-based MFA is widely used, a more secure alternative—number matching MFA—has emerged as the superior option. This blog post explains why number matching MFA is a better security measure than traditional push notifications and how it enhances protection against modern cyber threats.
Understanding Multi-Factor Authentication
Multi-factor authentication (MFA) is a security measure that requires users to provide multiple verification forms before accessing an account. This typically includes:
- Something You Know – A password or PIN.
- Something You Have – A smartphone, hardware token, or authentication app.
- Something You Are – Biometrics, such as fingerprint or facial recognition.
The goal of MFA is to add an additional layer of security, making it significantly harder for attackers to gain unauthorized access even if they obtain a user’s password.
Push Notification-Based MFA: A Security Gap
Push notification-based MFA is the most commonly used form of MFA. When a user attempts to log in, they receive a push notification on their registered device, which they can approve or deny, with a single tap of a button. While this method is convenient, it contains several security weaknesses:
- Susceptibility to MFA Fatigue Attacks
Attackers who obtain a user’s credentials may repeatedly attempt logins, causing an endless stream of authentication requests to the victim’s phone. This tactic, known as an MFA fatigue attack or prompt bombing, exploits human error or frustration. Users, overwhelmed by the barrage of notifications, might eventually approve a request unintentionally, granting attackers access.
- Accidental Approvals
Push notifications can be too easy to approve, especially if a user is distracted or in a hurry. Since many users habitually approve notifications without verifying details, attackers can take advantage of this behavior.
- Social Engineering Risks
Cybercriminals can use phishing or vishing (voice phishing) tactics, for example, to convince users to approve fraudulent login attempts. For instance, attackers might impersonate IT support and trick users into approving a login request, allowing unauthorized access.
Why Number Matching MFA is a Superior Alternative
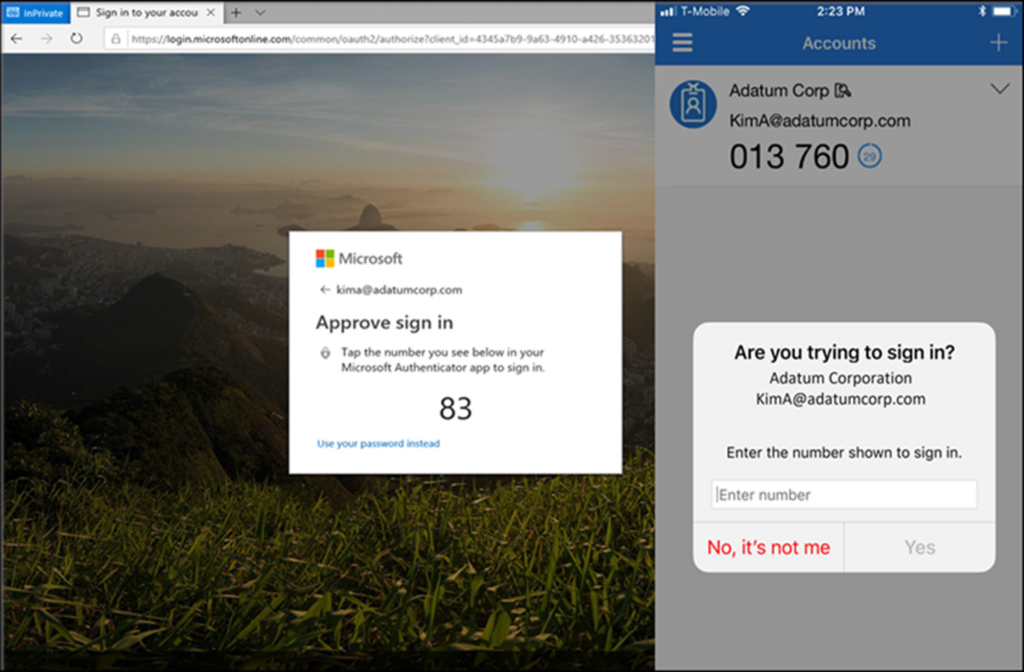
Number matching MFA significantly improves security by requiring users to verify a numerical code before approving authentication requests. Instead of simply clicking “Approve” on a push notification, users must match the number displayed on their login screen with the number presented in their authentication app. Here’s how this method is superior:
- Eliminates MFA Fatigue Attacks
Number matching prevents attackers from exploiting notification spamming. Since users must actively enter a code instead of passively approving a request, fatigue-based attacks become ineffective.
- Prevents Accidental Approvals
Unlike push notifications that users can approve without context, number matching requires users to consciously compare and input a code. This significantly reduces the likelihood of accidental approvals and enhances user awareness of authentication attempts.
- Stronger Defense Against Social Engineering
Even if an attacker attempts to trick a user into approving a fraudulent request, they cannot provide the correct number unless they have direct access to the user’s login screen. This makes social engineering attacks far less effective compared to standard push notifications.
- Encourages Security Awareness
By requiring users to actively verify authentication requests, number matching fosters better security awareness. Users become more mindful of their login attempts, helping them spot suspicious activity more effectively.
Adoption and Implementation
Several major authentication platforms, including Microsoft Authenticator and Duo Security, have implemented number matching as a security measure. Organizations looking to enhance their security should consider transitioning from traditional push notifications to number matching MFA. Here’s how they can do it:
- Update Authentication Policies – IT administrators should enforce number matching MFA as a mandatory authentication method across all user accounts.
- Educate Users – Conduct security awareness training to familiarize employees and users with the benefits and proper usage of number matching MFA as well as how and when to report suspicious login attempts.
- Monitor Authentication Logs – Regularly review login attempts and authentication logs to detect any unusual activity.
- Integrate with Existing Systems – Ensure that authentication apps and systems support number matching MFA for seamless adoption.
Conclusion
As cyber threats become more sophisticated, organizations and individuals must adopt stronger authentication methods. While push notification-based MFA has been a convenient choice, its vulnerabilities make it susceptible to modern attack techniques like MFA fatigue, accidental approvals, and social engineering.
Number matching MFA provides a far more secure alternative by requiring users to actively verify authentication requests, reducing the risks associated with traditional push notifications and human error. By adopting number matching MFA, organizations can significantly improve their security posture and protect against unauthorized access more effectively. For those who prioritize security, switching to number matching MFA is not just an upgrade, it’s a necessity.
